Cybersecurity
Cybersecurity has become an increasingly relevant topic in our daily lives due to the rise of technology and the growing amount of personal data stored online. Protecting our devices and data is essential to prevent the theft of confidential information and exposure to potential cyberattacks.
It is important to have a series of preventive measures, such as using strong passwords, regularly updating software and having an EDR
We should avoid sharing personal information on untrusted social media and platforms, and be aware of potential phishing or scam attempts through emails and text messages.
Companies must invest in security technologies and foster a culture of security among their employees, providing training and awareness about risks and best practices for protecting company data.
At Estratec360, we offer a cybersecurity-as-a-service model tailored to our clients' needs, with a team that responds immediately to their needs, both in protection and remediation of the damage caused, using state-of-the-art tools to provide the best service at your disposal.
Keeping our devices and data protected is essential to prevent potential attacks and protect our personal information.
In conclusion, cybersecurity is an issue of great importance in today's digital age.
Virtual Patching
What is virtual patching?
It involves implementing protective measures at the network or application layer that runs between the vulnerable system and the attacker. These measures can include firewall rules, web or application server configurations, or specific security policies that detect and block potential attacks.
Virtual patching is used as a temporary measure until a real patch can be applied to the system. This is useful when the time required to develop, test, and apply a real patch is too long, or when the company does not have access to the application's source code.
In short, virtual patching is a fast and effective solution for protecting an application or system from potential vulnerabilities and attacks until a real patch can be applied.
Cyberintelligence
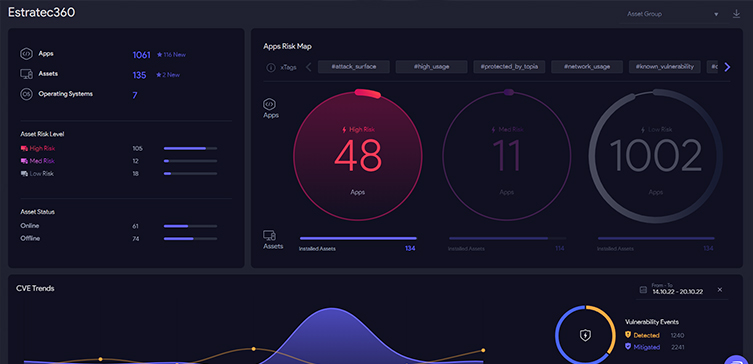
Cyber intelligence is a process by which relevant information about threats, vulnerabilities, and associated risks is collected and analyzed. It is used to identify and prevent cyberattacks and protect an organization's systems and data.
Preventing attacks by cybercriminals
We detect and prevent attacks before they occur, significantly reducing the risk of a security breach.
Early identification of vulnerabilities
Detecting and correcting vulnerabilities in your IT infrastructure before they can be exploited by cybercriminals.
Increasing the efficiency of security resources
Prioritizing and focusing your security resources on critical and vulnerable areas, maximizing their effectiveness and reducing costs.
Improved decision-making
Providing valuable information on threats and associated risks, enabling businesses to make strategic security decisions.
Regulatory compliance
Helps businesses comply with information security and privacy requirements established by government and industry laws and regulations.

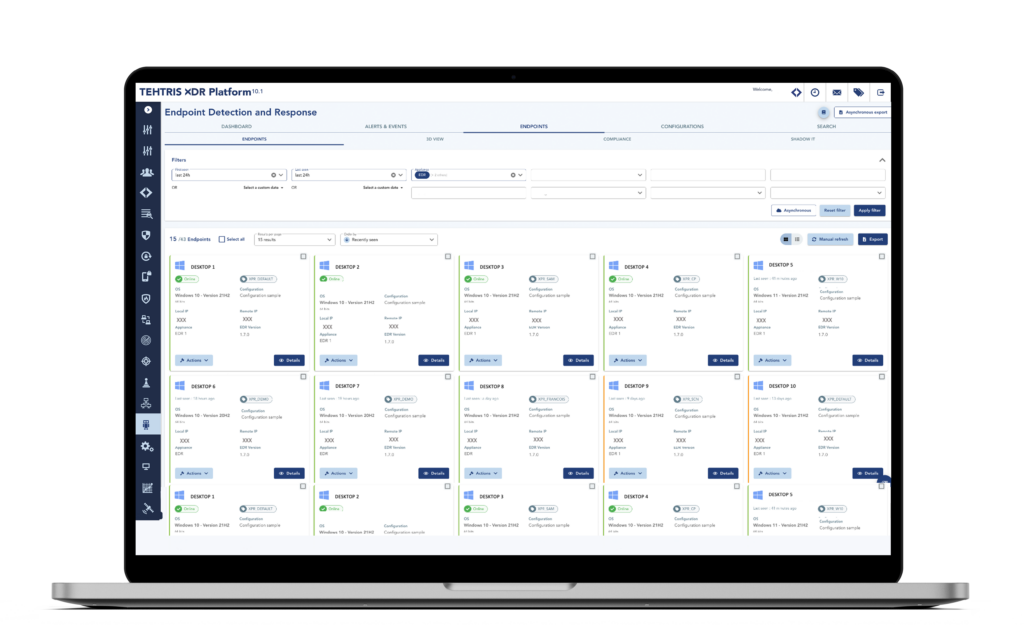
ANTIVIRUS AND EDR
Antivirus and EDR (Endpoint Detection and Response) are important tools for business IT security.
Antivirus programs detect and remove viruses and other malware from devices, while endpoint management programs monitor endpoints to detect and respond to advanced threats in real time.
Download our Cybersecurity Awareness Kit
What is a cybersecurity audit?
Whether it's to obtain an ISO certification (for example, 27001) or simply to understand the status of our environments, conducting a cybersecurity audit is essential.
A cybersecurity audit can be conducted internally or through third-party cybersecurity experts. During the audit, a detailed analysis of the organization's systems and networks is performed to identify potential vulnerabilities and security risks. Additionally, security policies and practices are evaluated to determine if they are aligned with industry best practices.
The audit results are used to develop an action plan to address the identified security issues. This plan may include updating systems, implementing new security policies and practices, training staff, and improving security infrastructure.


MDM
What is MDM?
MDM, or mobile device management, is a security solution used to protect a company's mobile devices. Through MDM, IT administrators can control employees' mobile devices, including smartphones and tablets, and apply security policies to ensure the protection of sensitive data and prevent unauthorized access. Typical MDM functions include mobile device monitoring and management, network access control, application management, and data wipe in the event of loss or theft. MDM is an essential tool for any company looking to protect its data and ensure the security of its employees.

